The Definitive Guide for Cyber Security Awareness
Table of ContentsThe 25-Second Trick For Cyber Security AwarenessThe smart Trick of Cyber Security Awareness That Nobody is Talking AboutThe 10-Minute Rule for Cyber Security AwarenessSee This Report about Cyber Security Awareness
As an example, an IT professional may suggest separating an unpatched medical device from the network (sequester) up until it might be patched, whereas the professional engineering specialist would certainly consider the danger vs. benefit of leaving the unpatched device on the network and pursuing another reduction method till the clinical device might be covered.The very first among these was the MDS2 (HIMSS MDS2, 2017) which consists of a lengthy listing of info about clinical devices safety and security attributes. Extra innovative and semiautomated CE-focused cybersecurity items are under advancement that scan a healthcare facility's network in real-time as well as incorporate that information with MDS2s, CMMS data, cyber threat data sources, and also gadget producer website to develop a cybersecurity-focused view of the HDO's device landscape (Asimily, 2017).
Data is vital in your day-to-day procedure, as well as data loss avoidance methods guarantee your information is readily available for your access in all times. Not simply any individual in your firm ought to have access to the company's delicate information. Accessibility and identification monitoring makes sure information is accessed just on a need-to-know basis which those acquiring the information are who they say they are.
actions taken to shield a computer or computer system (as on the web) versus unauthorized accessibility or strike 1989, in the meaning specified above Last Upgraded: 9 Sep 2022 Register for America's largest thesaurus and also get thousands a lot more meanings and advanced searchad cost-free!
Not known Facts About Cyber Security Awareness
New Zealand needs to be able to count on a strong cybersecurity labor force that's capable of protecting against, adjusting to, and reacting to cybersecurity dangers. This programme is designed to equip you with the core cybersecurity as well as technological abilities and also expertise you require to protect and handle information as well as systems safety.
For Study, Link purposes please ensure your application states your earliest program beginning date. For this program, you will require the following: Have effectively finished 120 debts of a degree 5 IT credentials or above or equivalent knowledge, abilities and experience Consent to Unitec taking on an Authorities clearance check, or a Criminal Document Inspect, and also suggest Unitec of any kind of existing fees or pending court matters A minimum of 8 debts at NCEA degree 2 in English (4 in Analysis, 4 in Composing), If English is not your mother tongue, you are needed to have several of the following: Have actually accomplished NCEA Degree 2 and also New Zealand College entryway Have the ability to give proof you satisfy our standards for existing English efficiency Have actually achieved at least one English effectiveness outcome in the last 2 years For more information on the training courses including schedules, please click the training course names listed below.
0 credit scores (0. 125 EFTS) This training course will certainly enable pupil to study, analyse, select and also use a variety of tools and also methods to create a remedy to a cybersecurity trouble. Wherever, possible pupils must carry out a task on part of a customer. 15. 0 credit ratings (0. 125 EFTS) This training course will make it possible for trainee to study, analyse, pick and also apply a series of tools and also techniques to create a remedy to a cybersecurity problem.
The details contained below is correct at the time of publishing, however as the programme review is continuous, the courses laid out may be liable to transform gradually - Cyber Security Awareness. Relax guaranteed that we will certainly alert you of any product changes to distribution that may affect what you research study, where you study or the methods you find out.
Little Known Facts About Cyber Security Awareness.

The cyber hazards these days are not the like even a couple of years earlier. As the cyber risk landscape adjustments, useful reference organizations require defense versus cybercriminals' existing and future devices and techniques. The cyber safety and security risk landscape is constantly evolving, and, periodically, these developments represent a new generation of cyber risks.

While collaborations and supplier connections are great for business, third-party users as well as software should have gain access to limited to the minimal required to do their work and also ought to be constantly checked. While ransomware has been around for years, it just became the dominant form of malware within the last few years.
Cyber Security Awareness Things To Know Before You Buy
Over the last few years, phishing strikes have only expanded a lot more innovative. While the original phishing scams were fairly very easy to find, modern strikes are persuading and sophisticated to the point where they can be virtually identical from reputable e-mails. Staff member cyber safety understanding training is not nearly enough to safeguard against the contemporary phishing hazard.
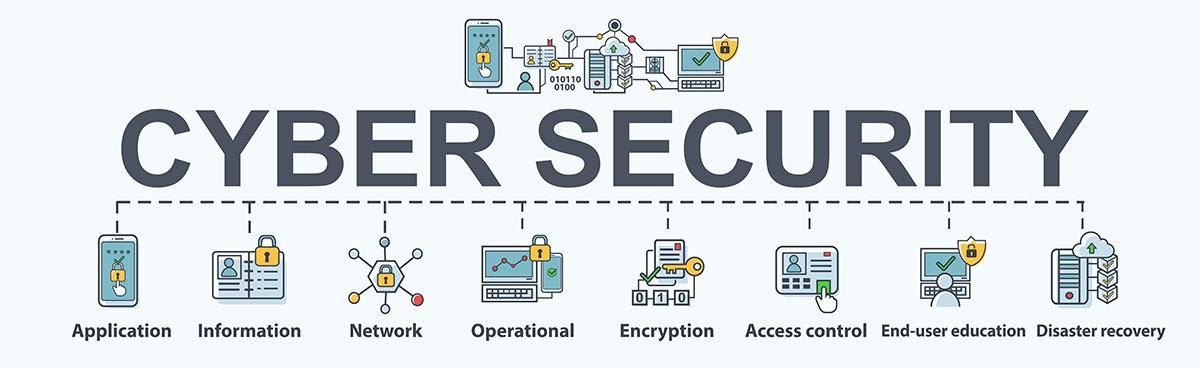
Malware strikes were much less usual and less advanced, and business frameworks were much less intricate. Today, cyber safety groups are usually overwhelmed while trying to manage these complicated cyber safety styles. This is brought on by a number of aspects, including: Modern cyberattacks can no much longer be identified with legacy methods to cyber protection.
As on-site employees. Trying have a peek here to fix all of these difficulties with a variety of separated solutions is unscalable and unsustainable.